The second quarter of 2022 was a significant and highly active quarter for ransomware gangs. We saw a noticeable rise in activity compared to Q1 2022, which had been a slow quarter for ransomware with a 25.3% decrease in activity. In this latest quarter, some of the biggest ransomware groups ceased operations, dangerous new gangs emerged, and operations continued to develop and evolve their tactics. We also observed many new tools being used to gain initial access and conduct attacks.
In this blog, we’ll examine some of the most significant ransomware stories from this quarter, assess new trends affecting the ransomware threat landscape, and speculate on how these changes will likely affect the third quarter of 2022.
KEY RANSOMWARE EVENTS Q2 2022
Conti’s fall
The most notable event of Q2 2022 was the fall of the “Conti” ransomware gang. Conti has been one of the most active ransomware groups since the creation of data-leakage websites and double extortion in early 2020. The group has been operating its data-leak site, “Conti.News”, since mid-2020, and they were considered one of the most experienced and successful ransomware groups active to date.
In May 2022, the gang announced that they were going to be shutting down operations, and the group stopped posting new victims to its data-leak site. The reason for Conti closing operations is unknown, but it is likely related to a leakage of internal chats that occurred in Q1 2022, where 60,000 internal messages from Conti were leaked.
Despite announcing that they were shutting down operations, the Conti.News data-leak site remained active until late-June 2022. The group allegedly continued to launch attacks and taunt the Costa Rican government on Conti.News, but these attacks were reportedly simply serving as a façade of running operations while Conti members moved on to other groups. Eventually, the group completely shut down all of its servers, including servers used to negotiate ransom payments with victims.
In this quarter, Conti was also finally overtaken by the LockBit ransomware gang for the total number of victims. This was a formidable record to beat, as Conti had reached close to 900 victims during its lifetime. LockBit is now nearing 1,000 victims at the time of writing, making them the most prolific group active to date.
LockBit linked to EvilCorp and PR stunt
A surprising revelation this quarter was that the cybercriminal group “EvilCorp” had allegedly begun to use LockBit ransomware in its attacks. By doing so, EvilCorp would have been able to avoid sanctions placed on the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC). This discovery was particularly threatening for LockBit, as any links to EvilCorp could result in U.S. victims refusing to make ransom payments, cutting profits in the group’s biggest target region.
LockBit responded to this accusation in a particularly unique way. The group named Mandiant on its data-leak site and claimed that it had stolen 356,841 files from the cyber company. LockBit created a countdown timer before the data was leaked, as the group usually does to give victims some time to respond, but for Mandiant, the post’s timer was set to expire on the same day the company was named. When the timer on LockBit’s site reached zero, the group released the alleged data, but it wasn’t Mandiant’s data, rather, they were text files with a statement from LockBit.

Mandiant named on LockBit data leak site
This statement denied Mandiant’s claims of EvilCorp working with LockBit. The ransomware group stated that the tools used by their affiliates could have been used by anyone, as the tools could be found in criminal forums, GitHub, and other public sources. LockBit also said that Maksim Yakubets, an EvilCorp member, had their own affiliate program for a narrow circle of “high class professionals”.
LockBit unleashes the new LockBit 3.0 ransomware
At last, one of the key stories of Q2 2022 was the release of LockBit 3.0, an improved version of one of the most successful ransomware operations active to date. This new version of LockBit came with many new improved capabilities and features. In particular, Lockbit created its own Bug-bounty program, where they are offering rewards for any exploits, personally identifiable information (PII), ideas, or information on high-value targets. They claim that payments start at USD 1,000 and go up depending on how valuable the information is.
The ransom note for LockBit’s new variant claims that LockBit 3.0 is the “world’s fastest and most stable ransomware”, and the group created new dark web sites for LockBit 3.0, which allows for the use of the Zcash cryptocurrency for payments. The new data-leak site also publicly displays ransom demands and allows anyone to purchase the data stolen from victims. Victims can also choose to pay to destroy all data stolen or pay to extend the timer for 24 hours.
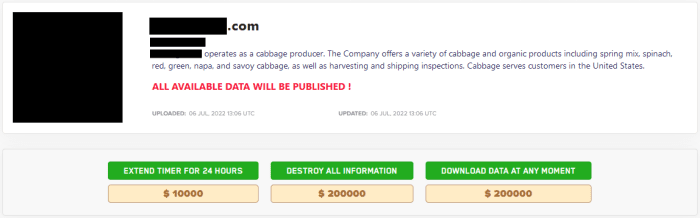
Victim posted on LockBit 3.0
Users in cybercriminal forums were initially skeptical of LockBit’s new bug bounty program. ReliaQuest observed threads on a Russian-speaking cybercriminal forum discussing LockBit’s new program and users stated that the offering from USD 1,000 was inadequate when compared to rewards offered by other marketplaces. Some users were also skeptical as to whether LockBit would actually pay for vulnerabilities disclosed, highlighting that the program could not attract many participants. LockBit replied to the thread assuring users that its program would pay users depending on how useful the vulnerability was for the group’s attacks.
Q2 2022 RANSOMWARE VICTIMS’ ANALYSIS
In Q2 2022, we observed a noticeable rise in ransomware activity, and many new data-leak sites were created. ReliaQuest monitors 88 data-leakage websites daily, providing an updated list of all new victims in our client portal. This coverage includes not only data-leak sites from ransomware groups, but also extortion groups like “Karakurt” and “LeakTheAnalyst”. However, incidents involving extortion groups are excluded from the numbers reported in this blog.
In Q2 2022, there were 705 organizations named to ransomware data-leakage websites. This was a 21.1 percent increase compared to last quarter, where we observed 582 victims. This increase was caused by an overall higher level of activity by most groups. Some noticeable increases came from “Alphv” (117.9% increase), “Vice Society” (100%), and “LockBit” (13.8%). There were also some groups who experienced less activity due to closures, such as Conti (37.4% decrease) and Hive Leaks (29.7%), who are believed to be linked to Conti.
BREAKDOWN BY GROUP

Ransomware activity by group Q2 2022
LockBit continued to be the most active group by an overwhelming margin. In Q2 2022, LockBit accounted for 32.77% of all incidents involving organizations being posted to ransomware data-leak sites, and the group broke a record for the highest number of victims in a quarter with 231 victims. LockBit had more than three times the number of victims as any other group. Conti still came in second, but unlike previous quarters, the second spot was tightly contested. Conti, Alphv, and Basta all had between 50 to 70 victims, making up 25.4% of all incidents combined. This was likely Conti’s last reign at the top, as the group has now closed operations.
The new and the old
Despite Conti departing this quarter, we saw the creation of many new groups that are likely to rival for that now-open second place spot that Conti had held for nearly a year. New groups that emerged and created data-leak sites included “Black Basta”, “Mindware”, “Cheers”, “RansomHouse”, “Industrial Spy”, “Yanluowang”, “Onyx”, “NOKOYAWA”, and “DarkAngels”. Black Basta has been one of the most successful newcomers, coming in 4th for the largest number of victims in the quarter.
In Q2, we also saw many groups shut down their data-leak websites. These consisted of Conti, “Pandora”, “Grief”, “Haron”, “Black Shadow”, “dotAdmin”, “HolyGhost”, and “Onyx”. Onyx created its data-leak site and shut it down within the same quarter. While these groups may have shut down their data-leak sites, it is still possible that they may be continuing operations and aim to create new sites in the future. Another significant event this past quarter was the return of Happy Blog, the data-leakage website of the “REvil” ransomware gang. Happy Blog’s return was surprising, given that its affiliates had been arrested in late 2021. New samples of the group’s ransomware suggest that REvil may have attempted to make a return. However, this return wasn’t highly successful, as the group failed to post more than five victims during the quarter.
ACTIVITY BY SECTOR
The Industrial Goods & Services sector was the most targeted sector in Q2 2022, with more than double the victims than the second most targeted sector.

Ransomware by victim sector Q2 2022
The industrial goods & services sector accounted for 18.4% of all attacks, remaining the most targeted sector in 2022. The second place was the technology sector (8.7% of incidents), followed by Construction & Materials (7.9%), Health Care (6.4%), and Government (5.5%) sectors.
For most sectors, the number of attacks increased significantly in Q2 2022. The technology sector saw a 117.9% increase in targeting, healthcare organizations had more than twice the number of victims compared to the last quarter (136.8% increase), and government entities experienced an increase in targeting by 56%. Critical sectors appeared to have faced the largest number of attacks in this quarter.
ACTIVITY BY GEOGRAPHY

Ransomware by victim geography Q2 2022
The United States remained the most often targeted nation, accounting for 38.9% of all victims. In comparison to Q1 2022, the number of victims in the nation grew by 35.6%. The US is likely to remain the most targeted nation in future quarters, given that it is considered the most profitable region for ransomware groups.
Second place went to Germany (up 66.7% from Q1 2022), which was followed closely by the United Kingdom (up 16.2%), Italy (up 6.7%), Canada (up 50%), and France (up 26.1%). Targeting increased over Q2 2022 in the majority of the nations.
Q3 2022 RANSOMWARE PROJECTIONS
In this final section, we will examine the events that are most likely to change the ransomware threat landscape in the upcoming quarter, as well as include projections for the next two quarters.
Q1 has historically been a quarter with low ransomware activity; therefore, it is not surprising that the number of ransomware attacks increased in Q2 2022. Several factors are likely to affect the number of ransomware activity in Q3 and Q4 2022, such as Conti’s closure and multiple sites shutting down. However, despite some of these events, it is likely that the number of ransomware attacks will continue increasing until Q4 2022, as new groups are created and begin gaining popularity.

Ransomware Victims by Month Forecast
When comparing Q2 ransomware activity to the same period as last year, we can also observe a noticeable rise in attacks in 2022. If this trend continues, then we could see record numbers at the end of the year.

Comparing Ransomware Victims in Q1 2021 and Q2 2022
One event that is likely to have a big impact in Q3 2022 is the release of LockBit’s new ransomware variant (LockBit 3.0). Last time that LockBit released a new and improved version of its ransomware, in July 2021, the group took over the ransomware threat landscape. If history repeats itself, then LockBit could possibly reach numbers higher than we have ever seen before over the next few quarters.
The new programs and features released by LockBit could also inspire other groups to follow in their footsteps, depending on the success of their new offerings. However, the group’s attempts at auctioning off the data are unlikely to be successful, as we have seen other groups such as REvil attempting similar tactics in the past without much success.
Conti’s closure is also another important event that occurred in Q2 2022. While the Conti ransomware gang ceased operations, that does not mean that Conti members are no longer conducting malicious activities. Rather, it is likely that Conti members broke down into smaller ransomware and extortion groups and will continue launching attacks under different names. By doing so, it becomes more difficult for law enforcement to shut down operations as one.
You can get a comprehensive look at the data that we used to build this blog with a free demo request of SearchLight here. You can additionally get a customized demo of ReliaQuest GreyMatter DRP to gain visibility of your organization’s threats and potential exposures, including access to a finished threat intelligence library with MITRE associations and mitigations from Photon Research.

LockBit’s Threat Intelligence profile in Searchlight
For further info—our previous blog article Tracking Ransomware Within SearchLight shows you how ReliaQuest GreyMatter DRP tracks emerging variants, enables you to export and block associated malicious indicators in various formats, instantly analyze popular targets, and map to your security controls with ease.