The ReliaQuest Photon Threat Research team has been investigating phishing attempts from the Initial Access Broker (IAB) “Exotic Lily” (also known as PROJECTOR LIBRA, TA580). IABs sell access to compromised networks, and this threat actor quickly achieved notoriety through their ties with ransomware groups such as “Conti” and “Diavol.” Exotic Lily specializes in gathering credentials from high-value targets through employee impersonation, deep open-source intelligence (OSINT), and by creating convincing malicious documents. Recently, the Photon team investigated an attack targeting one of our client’s high-ranking employees.
Exotic Lily has become particularly prevalent and successful due to the high level of detail they apply to their phishing campaigns. This has been seen repeatedly through a tried-and-tested path that typically begins with an open conversation to the victim, sourced from a fabricated business profile. These profiles then exploit this implied sense of trust to lure victims into navigating to seemingly benign sites to download malicious payloads.
Building Trust
The attack investigated by ReliaQuest started with an email sent to a profiled victim in the same business industry. The email in question sourced from what appeared to be a potential business prospect. Exotic Lily accomplished this by spoofing the domain of the legitimate organization they were posing as. In this case, the only difference between the legitimate organization (ex. company.com) and the spoofed company domain (ex. company.co) was the top-level domain (TLD).
In hindsight, you may think, “I would never fall for this,” but it’s important to show the victim empathy. Often, searching on the site company.co will lead the user to the legitimate site of company.com. This strengthens a false sense of trust between the threat actor and victim.
Sending the Phish
Once email communications are established, the threat actor is ready to move into the next stage of attack and deliver the malicious email. This is achieved typically by the group hosting a malicious zip file on a well-known filesharing platform (i.e., TransferNow, TransferXL, WeTransfer, OneDrive.) Next, this file is shared with the victim and an email is sent from the filesharing platform; because these emails originate from legitimate domains, they often make it into the victim’s inbox. After the victim has downloaded the zip file and extracted the contents, an ISO or IMG filetype is downloaded to the victim’s computer; ISO and IMG file types are used to clone the entire contents of a system disk.
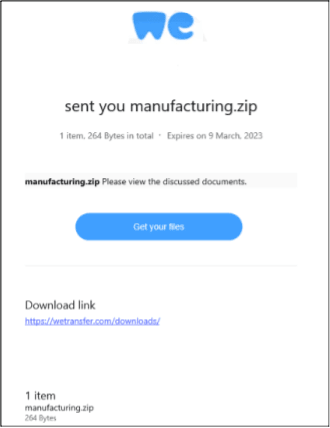
Now, the user must interact and mount either the IMG or ISO file, which will often contain an LNK file; this refers to a Windows Shortcut that serves as a pointer to open a file, folder, or application. Exotic Lily has been known to use Windows shortcuts to deploy the loader “BumbleBee”; loaders are used to load malicious content on the victim’s asset.
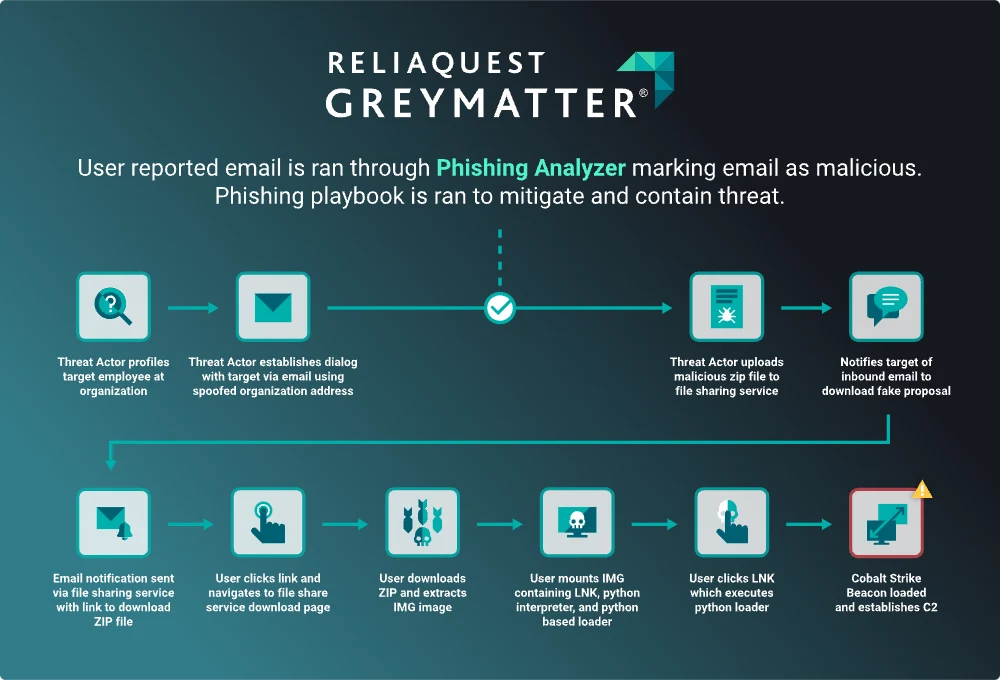
Recently though, the Photon Threat Research team investigated a unique case where a Python interpreter and Python-based loader were used instead of BumbleBee. When the user interacted with this LNK file, the packaged Python was executed, and a Cobalt Strike Beacon was loaded onto the victim’s machine. Shortly after, the beacon established a C2 channel and host enumeration began. This activity was short-lived, as the host was contained at this point.
What to Do If You’re Targeted
When a threat group such as Exotic Lily is targeting your company, it’s going to put your current security posture to the test. The level of expertise this IAB has is evident in each case the ReliaQuest Photon team investigates—such as deploying a Python interpreter and script to deploy a Cobalt Strike Beacon.
So, What Can You Do Today?
In 30 Days?
In 6 Months?
The GreyMatter Phishing Analyzer
The GreyMatter Phishing Analyzer will help improve your security team’s response time to user-reported phishing attacks. When such emails are reported, the Phishing Analyzer places key email artifacts under heavy scrutiny in the abuse mailbox. When a malicious verdict is reached, runbooks are performed to contain and mitigate the risk. Heightened user awareness combined with the GreyMatter Phishing Analyzer will prevent threat actors such as Exotic Lily from successfully phishing your end users. This frees up your security team from focusing on the manual efforts of a phishing investigation.
To learn more about the GreyMatter Phishing Analyzer, register for our upcoming democast.
Watch Phishing Analyzer in Action
To learn more about the email phishing landscape and see GreyMatter Phishing Analyzer in action, register for our upcoming democasts.







